Home Alone: OSINT Edition 🎅
Imagine how quickly "Home Alone" could've ended if police had modern tech!
Intro
Hi everyone! With the holidays just around the corner, I thought it would be the perfect time to revisit the classic story of “Home Alone”, but with a twist.
Instead of relying on Kevin’s wits alone, imagine a scenario where law enforcement could leverage powerful OSINT platforms to track down clues, verify identities, and end the mayhem in record time. In this video investigation and an explanation below, I’ll show how swiftly modern technology can piece together critical intel and save the day, proving that in the modern world, no one is left behind and everyone can be saved from criminals.
Video
Don’t forget to turn on the audio! A description of the investigation scenario is provided down below ⬇️
Scenario 🎥
Scene 1
What do we have? A boy left by his parents on Christmas. A boy home alone. Frightened.
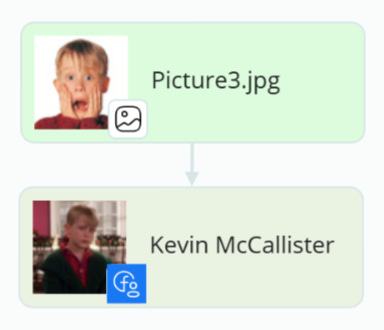
To help him, first, we need to find him. We know what he looks like, we know his name — in some cases that’s all we need. An investigator drags Kevin’s photo to SL CrimeWall, renames it and runs a method to search by face and name to find his FB account.
But that is not enough, we need more data and the officer runs a “Background Check” script on the account to get… wow! An email, a phone number, his family information (mom, dad, and 4 annoying siblings), a PIPL entry with a corresponding address (671 Lincoln Avenue, Winnetka, IL, USA), a few messengers and social network accounts, etc — the power of fake OSINT is incredible!
But, seriously, this is an important stage of any investigation if you search for a fictional character or not. It is essential to quickly gather the maximum amount of accurate information about the person of interest. And to achieve that, it is advantageous to use facial recognition and the most powerful open data providers.
Scene 2
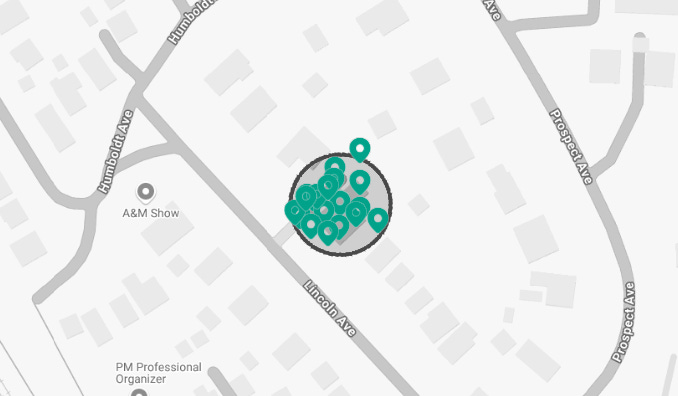
What’s next? Kevin’s parents left him home alone, which leads a competent investigator to an assumption that the presence of other people in his house would be suspicious and unlikely. There are many methods to search for posts, groups and people starting from the area (coordinates) but let’s open our lawful interception bag of presents and take a cell phone geolocation tool out of it. If we select an area and run this method in monitoring mode we will be able to determine who visited Kevin and when.
Seasons change, time passes by… Well, days. Retrospectively in Map View, we see new pins appear near the house. Kevin himself, neighbour, Uber Eats delivery guys. Geofencing is incredibly effective for tracking the location of criminals and monitoring activity in a specific area. All you need is a phone number.
Scene 3
But how do we find Wet Bandits? The answer is chronolocation, we — I mean an officer — will use Timeline to select a period of nighttime when any new phones in the area will raise suspicion. And yes, only 3 phones were detected on the property: first — Kevin’s, other ones — unknown.
An officer returns to the graph and sees that 2 phones in a group of many and a separate single one are selected and shown in the CrimeWall Navigation tab. He deselects the separate one (it’s Kevin’s) and runs “[SL ISE] Search by Phone” method to look for corresponding data leaks.
And there are two, camera zooms in, drumroll — Harry and Marv are BUSTED!
Searching and mapping existing information with records from data leaks allows for a quick pivot to uncover real names and even photos of suspects. This functionality often helps break through dead ends and solve cases.
Outro
I hope you enjoyed this simple yet vivid story. Wishing you and your family a safe and merry Christmas! 🎄
A huge thanks to the Social Links CrimeWall team for their incredible efforts in developing tools that make our lives much safer and turn scenarios like Home Alone into an incredible fairy tale. ❤️







COOL!